Cyber-attack: Europol says it was unprecedented in scale
A digital assault that hit associations overall including the UK's National Health Service was "phenomenal", Europe's police office says.
Europol likewise cautioned a "mind boggling universal examination" was required "to recognize the guilty parties".
Ransomware encoded information on no less than 75,000 frameworks in 99 nations on Friday. Installments were requested for access to be reestablished.
European nations, including Russia, were among the most exceedingly terrible hit.
In spite of the fact that the spread of the malware - known as WannaCry and variations of that name - seems to have impeded, the danger is not yet over.
Europol said its digital wrongdoing group, EC3, was working intimately with influenced nations to "alleviate the danger and help casualties".
In the UK, the leader of the digital security office said specialists were "working day and night" to reestablish the frameworks of nearly 45 NHS associations that were hit by the assault.
The assault left healing centers and specialists not able to get to patient information, and prompted the cancelation of operations and medicinal arrangements.
Who else has been influenced by the assault?
A few reports said Russia had seen a larger number of contaminations than some other single nation. Household banks, the inside and wellbeing services, the state-claimed Russian railroad firm and the second-biggest cell phone system were altogether answered to have been hit.
Russia's inside service said 1,000 of its PCs had been tainted yet the infection was quickly managed and no touchy information was traded off.
In Spain, various huge firms - including telecoms monster Telefonica, control firm Iberdrola and utility supplier Gas Natural - were additionally struck, with reports that staff at the organizations were reprimanded to turn their PCs.
Individuals tweeted photographs of influenced PCs including a nearby railroad ticket machine in Germany and a college PC lab in Italy.
France's carmaker Renault was compelled to stop generation at various destinations. Portugal Telecom, the US conveyance organization FedEx and a nearby expert in Sweden were likewise influenced.
China has not formally remarked on any assaults it might have endured, yet remarks via web-based networking media said a college PC lab had been traded off.
Incidentally, fund priests from the G7 gathering of driving mechanical nations had been meeting on Friday to examine the risk of digital assaults.
They promised to work all the more nearly on spotting vulnerabilities and surveying safety efforts.
How could it happen and who is behind it?
The malware spread rapidly on Friday, with restorative staff in the UK allegedly observing PCs go down "one by one".
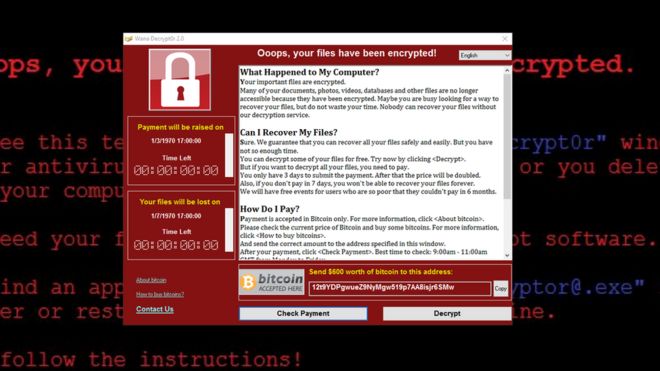
NHS staff shared screenshots of the WannaCry program, which requested an installment of $300 (£230) in virtual money Bitcoin to open the records for every PC.
The contaminations appear to be sent by means of a worm - a program that spreads without anyone else's input between PCs.
Most different pernicious projects depend on people to spread by deceiving them into tapping on a connection harboring the assault code.
By difference, once WannaCry is inside an association it will chase down helpless machines and contaminate them as well.
It is not clear who is behind the assault, but rather the instruments used to complete it are accepted to have been produced by the US National Security Agency (NSA) to abuse a shortcoming found in Microsoft's Windows framework.
This endeavor - known as EternalBlue - was stolen by a gathering of programmers known as The Shadow Brokers, who made it uninhibitedly accessible in April, saying it was a "dissent" about US President Donald Trump.
A fix for the defenselessness was discharged by Microsoft in March, which would have naturally secured those PCs with Windows Update empowered.
Microsoft said on Friday it would reveal the refresh to clients of more established working frameworks "that at no time in the future get standard support", such Windows XP (which the NHS still to a great extent utilizes), Windows 8 and Windows Server 2003.
The quantity of diseases is by all accounts abating after an "off button" seems to have been incidentally activated by a UK-based digital security analyst tweeting as @MalwareTechBlog.
He was cited as saying he saw the web address the infection was hunting down had not been enlisted - and when he enrolled it, the infection seemed to quit spreading.
In any case, he cautioned this was an impermanent settle, and encouraged PC clients to "fix your frameworks ASAP".
Why do organizations still utilize Windows XP? By Chris Foxx, innovation columnist
Many occupations should be possible utilizing programming everybody can purchase, yet a few organizations require programs that perform particular employments - so they manufacture their own.
For instance. a telecaster may require authority programming to track all the satellite bolsters coming into the newsroom, and a doctor's facility may require custom-fabricated instruments to break down X-beam pictures.
Creating specialty yet valuable programming like this can be extremely costly - the programming, testing, upkeep and proceeded with improvement all includes.
At that point along comes another rendition of Windows, and the product isn't good. Organizations then face the cost of updating PCs and working framework licenses, and the cost of modifying their product starting with no outside help.
In this way, some continue running the old adaptation of Windows. For a few organizations, that is not an enormous hazard. In a clinic, the stakes are higher.
Loading...

No comments